Building the Same App across Various Web Frameworks
Eugene Yan
SEPTEMBER 7, 2024
Comparing five implementations built with FastAPI, FastHTML, Next.

Eugene Yan
SEPTEMBER 7, 2024
Comparing five implementations built with FastAPI, FastHTML, Next.

insideBIGDATA
SEPTEMBER 7, 2024
Protect AI, a leading artificial intelligence (AI) and machine learning (ML) security company, announced the availability of MLSecOps Foundations, a free four part video training and certification program on how to build security into AI/ML led by its CISO Diana Kelley.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Hacker News
SEPTEMBER 7, 2024
Another Google antitrust trial starts on Monday. If Google loses, it'll be three strikes. At some point, they will give up and realize that the writing is on the wall for their current business model.
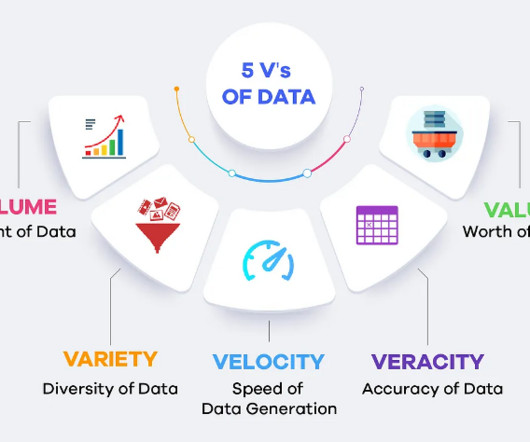
Women in Big Data
SEPTEMBER 7, 2024
The Power of Big Data transcends the business sector. It moves beyond the vast amount of data to discover patterns and stories hidden inside. By leveraging big data, organizations and institutions can uncover valuable insights, predict trends, and make informed decisions that significantly influence their strategic directions and operational efficiencies.

Advertisement
Apache Airflow® 3.0, the most anticipated Airflow release yet, officially launched this April. As the de facto standard for data orchestration, Airflow is trusted by over 77,000 organizations to power everything from advanced analytics to production AI and MLOps. With the 3.0 release, the top-requested features from the community were delivered, including a revamped UI for easier navigation, stronger security, and greater flexibility to run tasks anywhere at any time.

Hacker News
SEPTEMBER 7, 2024
Academic journals, archives, and repositories are seeing an increasing number of questionable research papers clearly produced using generative AI. They are often created with widely available, general-purpose AI applications, most likely ChatGPT, and mimic scientific writing. Google Scholar easily locates and lists these questionable papers alongside reputable, quality-controlled research.
Hacker News
SEPTEMBER 7, 2024
LLM chatbots can be engaged in endless "conversations" by considerably simpler text generation bots. This has some interesting implications.
Data Science Current brings together the best content for data science professionals from the widest variety of thought leaders.

Hacker News
SEPTEMBER 7, 2024
If not the most famous artwork in the world, it is certainly one of the most famous.

Hacker News
SEPTEMBER 7, 2024
Citizen DJ invites the public to make music using free-to-use audio and video collections. By embedding these materials in hip hop music, listeners can discover items in the library's vast collections that they likely would never have known existed.

Hacker News
SEPTEMBER 7, 2024
Genius is fragile. Success, even more so. What does it mean then for an artist to fail?

Speaker: Tamara Fingerlin, Developer Advocate
Apache Airflow® 3.0, the most anticipated Airflow release yet, officially launched this April. As the de facto standard for data orchestration, Airflow is trusted by over 77,000 organizations to power everything from advanced analytics to production AI and MLOps. With the 3.0 release, the top-requested features from the community were delivered, including a revamped UI for easier navigation, stronger security, and greater flexibility to run tasks anywhere at any time.

Hacker News
SEPTEMBER 7, 2024
He stressed that cybercrime issues, such as gambling, prostitution and pornography websites, demand comprehensive solutions.

Hacker News
SEPTEMBER 7, 2024
Before modern air travel and first-class suites, the grandest thing in luxury air travel was the German Zeppelin airship.

Hacker News
SEPTEMBER 7, 2024
Comment directly on top of arXiv papers.

Advertisement
In Airflow, DAGs (your data pipelines) support nearly every use case. As these workflows grow in complexity and scale, efficiently identifying and resolving issues becomes a critical skill for every data engineer. This is a comprehensive guide with best practices and examples to debugging Airflow DAGs. You’ll learn how to: Create a standardized process for debugging to quickly diagnose errors in your DAGs Identify common issues with DAGs, tasks, and connections Distinguish between Airflow-relate

Hacker News
SEPTEMBER 7, 2024
Server racks as home furniture.
Hacker News
SEPTEMBER 7, 2024
‘For better or worse, we’re stuck with each other. I think for the better.

Hacker News
SEPTEMBER 7, 2024
Comments

Speaker: Alex Salazar, CEO & Co-Founder @ Arcade | Nate Barbettini, Founding Engineer @ Arcade | Tony Karrer, Founder & CTO @ Aggregage
There’s a lot of noise surrounding the ability of AI agents to connect to your tools, systems and data. But building an AI application into a reliable, secure workflow agent isn’t as simple as plugging in an API. As an engineering leader, it can be challenging to make sense of this evolving landscape, but agent tooling provides such high value that it’s critical we figure out how to move forward.

Hacker News
SEPTEMBER 7, 2024
Sometimes I just want to put pixels on a screen. I don’t want to think about SDL this or OpenGL that—I just want to draw my pixel buffer and be done.

Speaker: Andrew Skoog, Founder of MachinistX & President of Hexis Representatives
Manufacturing is evolving, and the right technology can empower—not replace—your workforce. Smart automation and AI-driven software are revolutionizing decision-making, optimizing processes, and improving efficiency. But how do you implement these tools with confidence and ensure they complement human expertise rather than override it? Join industry expert Andrew Skoog as he explores how manufacturers can leverage automation to enhance operations, streamline workflows, and make smarter, data-dri

Hacker News
SEPTEMBER 7, 2024
While C tends to be the go-to launguage for microcontrollers, Raspberry Pi is promoting the prospects of using Rust on their RP2350 microcontroller.

Hacker News
SEPTEMBER 7, 2024
I got an email the other day from mathematician Bogdan Grechuk, whose book Polynomial Diophantine Equations: A Systematic Approach ([link] was recently released. This is to my mind a rather remarkable book.

Hacker News
SEPTEMBER 7, 2024
Comments

Speaker: Frank Taliano
Documents are the backbone of enterprise operations, but they are also a common source of inefficiency. From buried insights to manual handoffs, document-based workflows can quietly stall decision-making and drain resources. For large, complex organizations, legacy systems and siloed processes create friction that AI is uniquely positioned to resolve.

Hacker News
SEPTEMBER 7, 2024
The 1000 most popular books on Hacker News visualized on an interactive map.

Hacker News
SEPTEMBER 7, 2024
DNS "propagation" is actually caches expiring

Hacker News
SEPTEMBER 7, 2024
Comments

Advertisement
With Airflow being the open-source standard for workflow orchestration, knowing how to write Airflow DAGs has become an essential skill for every data engineer. This eBook provides a comprehensive overview of DAG writing features with plenty of example code. You’ll learn how to: Understand the building blocks DAGs, combine them in complex pipelines, and schedule your DAG to run exactly when you want it to Write DAGs that adapt to your data at runtime and set up alerts and notifications Scale you
Let's personalize your content